Encryption protects your data. It protects your data when at rest on your device, and it protects your data when in transit - around the corner or around the world. It protects your conversations, whether voice or text. And sometimes, it protects your life.
But comprehensive protection against today’s wide range of threats requires more than just encryption. It requires the device you entrust your data with to be worthy of that trust. It requires the device to withstand attacks against itself.
To achieve this, all GSMK CryptoPhones are based on a “hardened” operating system with streamlined, security-optimized components and communication stacks. The hardened operating system is designed to protect the device against outside attacks, thus offering true 360-degree protection when it counts most.

Telecommunication Interception
The vast amount of data collected and accessible to modern intelligence support systems on the one hand, and increasingly inexpensive tactical interception systems (“IMSI catchers”) on the other hand have effectively rendered the privacy of regular telephone calls and electronic messages an illusion.
Major factors contributing to electronic surveillance on this unprecedented scale are long-running vulnerabilities in Signaling System No. 7 (“SS7”) and Diameter, the signaling protocols used to interconnect today’s telephone networks, as well as the combination of increased processing power for content analysis and steadily falling costs for that same processing power. With it having become standard practice for intelligence agencies to indiscriminately record all calls made in a given country in a given year, and the accompanying databases and analysis tools being well capable of matching these recording capabilities, it has become increasingly easy to find the proverbial needle in the haystack.
Identifying crucial information, context, and communication relationships requires little, if any, manual intervention. If you thus ask yourself who is intercepting your communication, the answer is straightforward: Nobody. It’s all done by computers and the algorithms they have been programmed with.

Air Interface Insecurity
Standard network security measures that are supposed to protect mobile telephone calls from eavesdropping have long been known to be weak. The standard encryption algorithms that were supposed to protect regular GSM mobile telephone calls from eavesdropping have long been compromised. Today, the technology to crack GSM’s standard encryption algorithm is accessible even to amateurs at moderate cost. Subsequent network generations like UMTS, LTE and 5G have introduced considerable improvements in authentication, encryption, and integrity protection. However, interception equipment has kept pace with these improvements, effectively neutralizing attempts to secure the air interface from mobile phone to mobile base station.
Active, semi-active, and passive tactical interception systems continue to be able to monitor mobile phones on the air interface level. “IMSI catchers” can be used to determine the electronic identities (the International Mobile Subscriber Identity (IMSI) as well as other information identifying a particular mobile phone) of all mobile phones in their vicinity, facilitating their easy identification at any point in the telephone network. Some systems are also capable of over-the-air injection of advanced spyware that stays resident on the victim’s mobile phone.
What is needed in this environment are phone platforms that are protected against any third party attempting to monitor or take control of the phone and inject malicious code. GSMK CryptoPhones not only offer end-to-end encryption of calls and messages, their encrypted traffic is also camouflaged to protect communication from being tracked. With no meta data to be analyzed, communication relationships remain private.

Encryption
GSMK CryptoPhone technology is based on published and well researched algorithms for both encryption and voice processing. All GSMK CryptoPhones use the same encryption engine with proven algorithms and very long keys, resulting in products that provide peace of mind today and in the future.
A Unique Cryptographic Safety Net
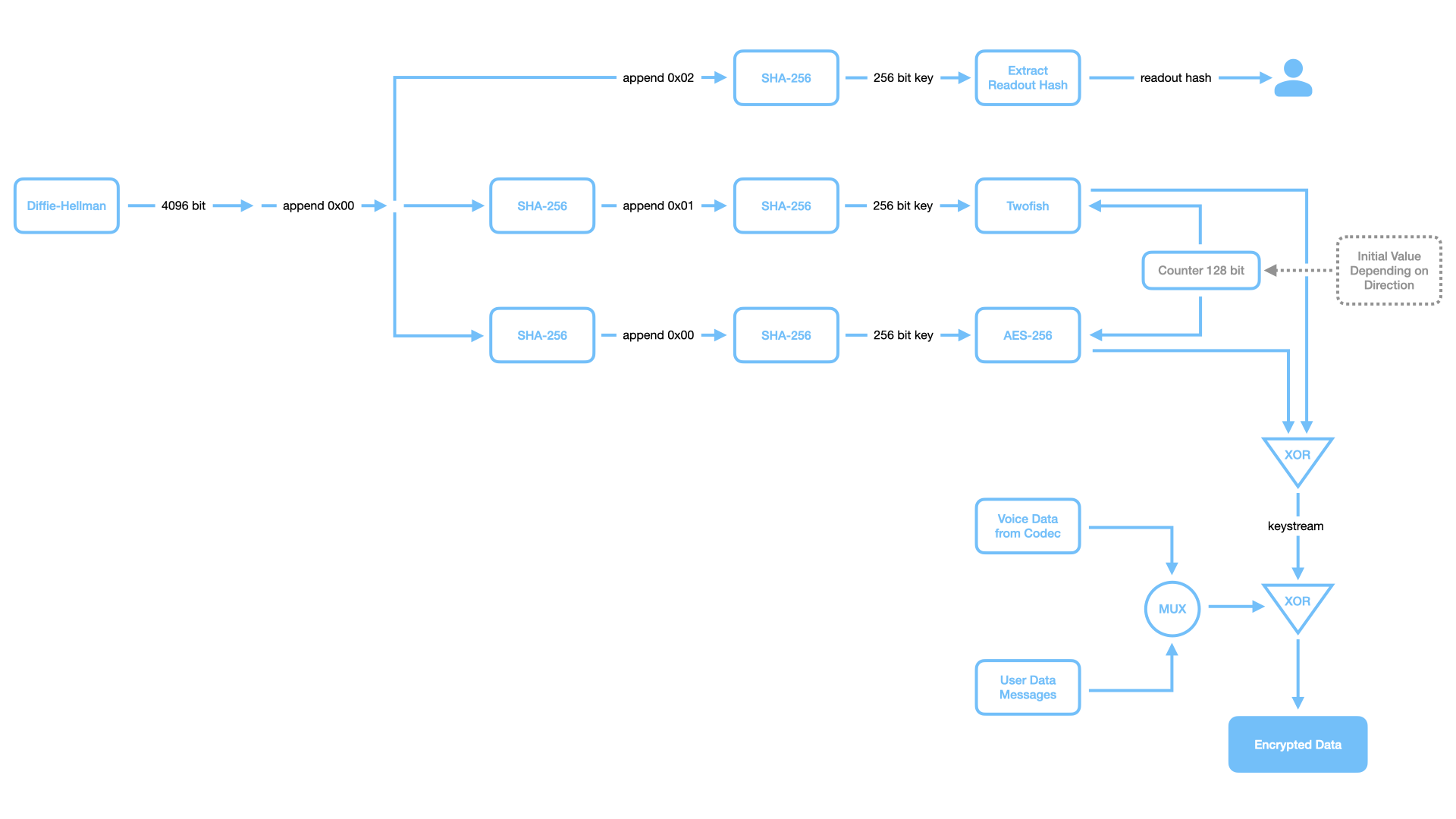
All calls are encrypted with 256-bit keys using AES and Twofish running as counter mode stream ciphers. Using both AES and Twofish provides a much stronger design than using only one algorithm. For the highly unlikely case that a weakness is discovered in one of the algorithms, the use of the second algorithm provides an additional “safety net” and results in a higher security margin. The use of these two very strong algorithms is a unique feature of GSMK CryptoPhones that provide a “fall back” inside the crypto-system design.
The design goal was to provide not only “tactical security” that lasts for a few months or years, but to design for security against future developments in cryptanalysis in the next decades.
Prevention of Man-in-the-Middle Attacks
The key used for each call is generated using a 4096-bit Diffie-Hellman shared secret exchange, hashing the resulting 4096 bits to the 256 bit session key by means of SHA256. To prevent man-in-the-middle attacks, a six-letter hash is generated from the Diffie-Hellman result and displayed to the user. The user then reads three letters over the encrypted line to the communication partner and verifies the three letters the communication partner reads to him. Verification of the hash ensures that both parties use the same key and that no man-in-the-middle attack was carried out. The Diffie-Hellman key agreement module in the CryptoPhone Security Kernel implements an early commitment scheme that requires both parties to send a hash of their computed secret value early in the exchange process in order to prevent a man-in-the-middle attacker from a brute-force calculation of his own private key.
Enhanced Entropy
GSMK CryptoPhones use a true random number generator for generating private keys. To obtain true random numbers, the calling application provides the RNG with a 128-bit seed value and a 128-bit seed key, and the RNG produces 128-bit blocks of random values that are ultimately used as the Diffie-Hellman private key. The seeding material for the RNG is provided to the cryptographic module by means of using the least significant bit (LSB) from the microphone signal prior to the actual call, clock skew, and additional sources of entropy. This scheme ensures that each key exchange is performed with a completely new and truly random key.
Forward Secrecy
GSMK CryptoPhones offer perfect forward secrecy for encrypted voice calls by ensuring that all key material is securely erased immediately after the call ends. As a consequence, in the event that the user and/or the device is captured, neither can be forced to reveal keys that compromise earlier secure voice communications.
Secure Messaging
For encrypted messaging, the result of an initial key exchange is stored in the secure storage container on the phone and used by means of a hash-chain.

More than Encryption
360-degree communications security requires far more than just encryption. It needs a solid foundation in the form of a protected device as the interface needed for content decryption. To ensure integrity under attack, our products come with a hardened operating system capable of defending the device against attempts to compromise or gain unauthorized access to it.
Metadata
Using the proprietary CryptoPhone IP communications protocol, connections are camouflaged to protect metadata and deny an attacker the opportunity to trace your calls. As a result, an observer is not only unable to intercept calls or messages, but is also unable to determine who is speaking with whom. In combinations, these measures taken together ensure that both data in transit and data at rest remain private and secure.
Baseband Firewall
Cellular devices are in addition equipped with the GSMK Baseband Firewall (BBFW), which repels highly advanced attacks against the radio module of the phone. The BBFW, based on GSMK-patented technology and an industry first, is a dedicated security module integrated in all current-generation CryptoPhone mobile phones, such as the CP700 protecting the integrity of the phone against over-the-air attacks involving rogue base stations. The outcome of a decade of research undertaken by GSMK, it makes GSMK CryptoPhones the only mobile phones in the world capable of defending themselves against sophisticated attacks against the phone’s baseband processor.
The BBFW module thus helps fulfill the promise of true 360-degree security, namely that the communication link as well as the mobile device itself must not be penetratable by adversaries. Sophisticated threat actors will try to circumvent a device’s encryption mechanisms by gaining access to the phone’s baseband processor in order to e.g. obtain unencrypted voice straight from the microphone, well before it is encrypted, and exfiltrate that data via one of the network interfaces controlled by the baseband processor.
The BBFW is the only security component available on the global market capable of not only identifying such attacks and warning the user of the presence of IMSI catchers and other rogue base stations, but also of taking countermeasures to ensure that attempts to inject malware over the air interface are thwarted at an early stage. It is this kind of comprehensive protection also against very sophisticated attacks that is the hallmark of GSMK’s 360-degree protection strategy - giving you peace of mind to fully concentrate on your work.
Reliability
Many of our customers all over the world operate their CryptoPhone systems under very challenging network conditions. With years of experience in deploying secure mobile communication systems in over 50 countries worldwide, GSMK has designed its signature CryptoPhone IP secure communications protocol to work over any transport layer that can provide a minimal IP connection. The required bandwidth for secure voice communications is less than 5 kbps, ensuring that an encrypted call will go through even on a badly overloaded local network or a poorly maintained rural commercial 2G GPRS network. The CryptoPhone IP system’s robust design allows it to easily handle jitter as well as the typical delays of satellite connections. Thanks to camouflaged traffic, CryptoPhone IP stays under the radar and works even in areas where traditional SIP VoIP-based products are blocked or quality-degraded by the network.
Whether on the road using a cellular phone, in a joint situation room with IP-based infrastructure, in the desert or onboard a naval vessel with a narrowband satellite connection, or in a remote village with only an analog line, the GSMK CryptoPhone® secure communications system offers reliable multi-network, multi-platform secure communications across network borders.
CryptoPhone Source Code
Transparency is a cornerstone of trust. GSMK CryptoPhones have been formally approved for the transmission of sensitive and classified information in a great many countries worldwide. Yet you do not have to rely on external certification bodies to assess the security and trustworthiness of your secure communications system:
GSMK CryptoPhones are the only secure phones on the market with source code being made available for independent security assessments. This permits individual source code audits in accordance with national and international verification and certification standards designed to verify device integrity mechanisms, correct implementation of all encryption algorithms, and the absence of backdoors.
The source code is the collection of computer instructions written in human-readable programming language, specifying actions to be performed by the CryptoPhone. Source code inspections are usually performed as one of the last technical evaluation steps in a procurement process, usually run by the customer’s in-house specialists, but sometimes also by external consultants.
We pride ourselves in having passed all source code inspections to the full satisfaction of our respective customers. Such inspections typically mark the beginning of a long relationship built on trust and mutual respect. We invite you to contact us to make the same come true for your organization.
More questions? Please see the FAQs or contact us.
